
A New Threat to Web Servers: HTTP/2 CONTINUATION Flood Vulnerability:
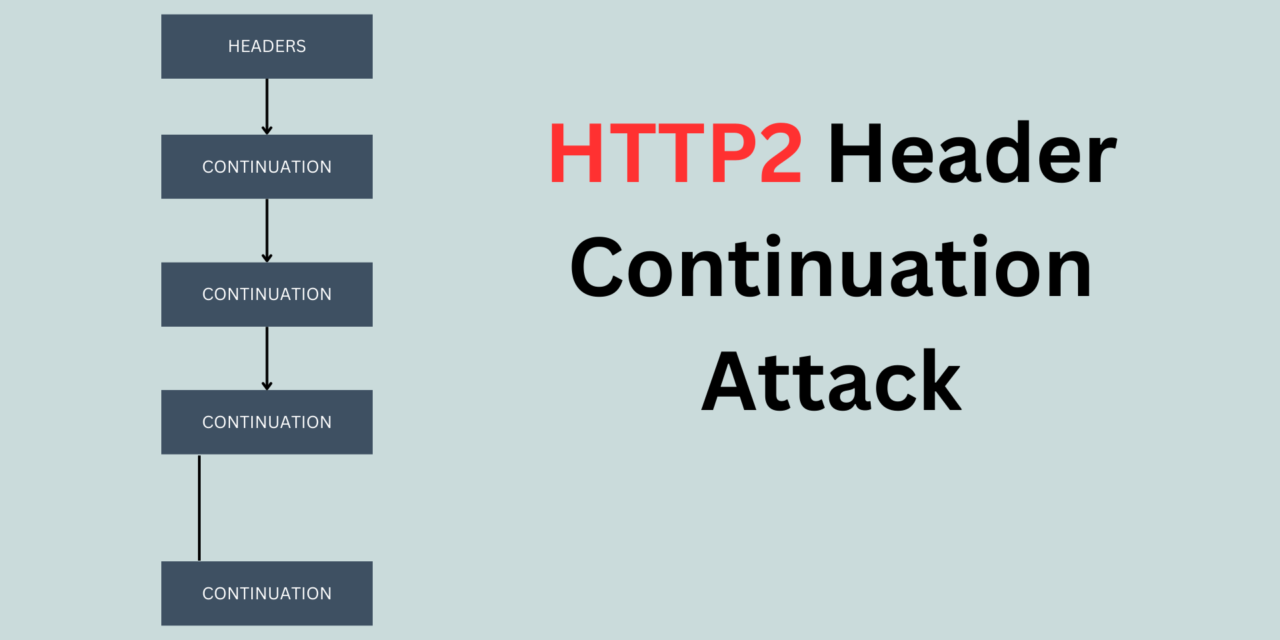
Introduction:
Recent research has uncovered a critical vulnerability in the HTTP/2 protocol, known as the CONTINUATION Flood, which poses a significant risk to web servers. This vulnerability, discovered by security researcher Bartek Nowotarski, exploits flaws in the handling of CONTINUATION frames, potentially enabling denial-of-service (DoS) attacks with severe consequences for server availability and performance. In this article, we delve into the intricacies of the HTTP/2 CONTINUATION Flood vulnerability, its impact on web servers, and strategies for mitigating this emerging threat.
Understanding the HTTP/2 Protocol:
HTTP/2, introduced in 2015, represents a significant advancement over its predecessor by enhancing web performance through features such as binary framing, multiplexing, and header compression. However, the complexity of the protocol introduces new challenges, as evidenced by the discovery of vulnerabilities like the CONTINUATION Flood.
Exploring the Vulnerability:
The CONTINUATION Flood vulnerability arises from inadequate checks and limitations on CONTINUATION frames within HTTP/2 implementations. These frames, designed to stitch together fragmented header blocks, can be exploited by attackers to overwhelm servers with an excessive stream of frames lacking the ‘END_HEADERS’ flag, leading to memory exhaustion, CPU overload, and ultimately, server crashes.
Implications of Exploitation:
The exploitation of the HTTP/2 CONTINUATION Flood vulnerability can have dire consequences for web servers. By leveraging a single TCP connection, attackers can launch DoS attacks capable of incapacitating servers, disrupting services, and causing widespread outages. Furthermore, the stealthy nature of the attack, with malicious requests often going undetected in access logs, complicates mitigation efforts.
Assessing Vulnerable Implementations:
Numerous HTTP/2 implementations have been identified as susceptible to CONTINUATION Flood attacks, each presenting unique risks and vulnerabilities. From Node.js and Envoy to Apache Httpd and beyond, the list of affected implementations underscores the widespread nature of this security flaw.
Mitigating the Threat:
Addressing the HTTP/2 CONTINUATION Flood vulnerability requires a multifaceted approach encompassing both immediate remediation steps and long-term preventive measures. Key strategies include implementing proper frame validation and limiting the size and frequency of CONTINUATION frames, as well as deploying intrusion detection systems and conducting regular security audits.
Proposed Solutions:
To mitigate the risk posed by the CONTINUATION Flood vulnerability, HTTP/2 implementations must prioritize security patches and updates addressing specific CVEs associated with the flaw. Additionally, organizations should invest in robust cybersecurity frameworks and practices to fortify their defenses against evolving threats.
Conclusion:
The discovery of the HTTP/2 CONTINUATION Flood vulnerability serves as a stark reminder of the ongoing battle to secure web infrastructure against malicious actors. As the digital landscape continues to evolve, vigilance, collaboration, and proactive risk management are essential in safeguarding the integrity and resilience of web servers worldwide. By addressing vulnerabilities promptly and adopting a proactive security posture, organizations can mitigate the risks posed by emerging threats and ensure the continued availability and reliability of their online services.
Sources:
https://nowotarski.info/http2-continuation-flood-technical-details/
https://thehackernews.com/2024/04/new-http2-vulnerability-exposes-web.html









